What is business email compromise?
Business email compromise (BEC), alternatively known as email account compromise (EAC), is a type of cybercrime that uses email fraud to target companies, businesses, and corporations. Business email compromise scams involve scammers sending emails to company employees with certain requests, such as making a money transfer. Because they are able to successfully pretend to be authentic senders, cybercriminals are able to scam businesses out of thousands if not millions of dollars every year.
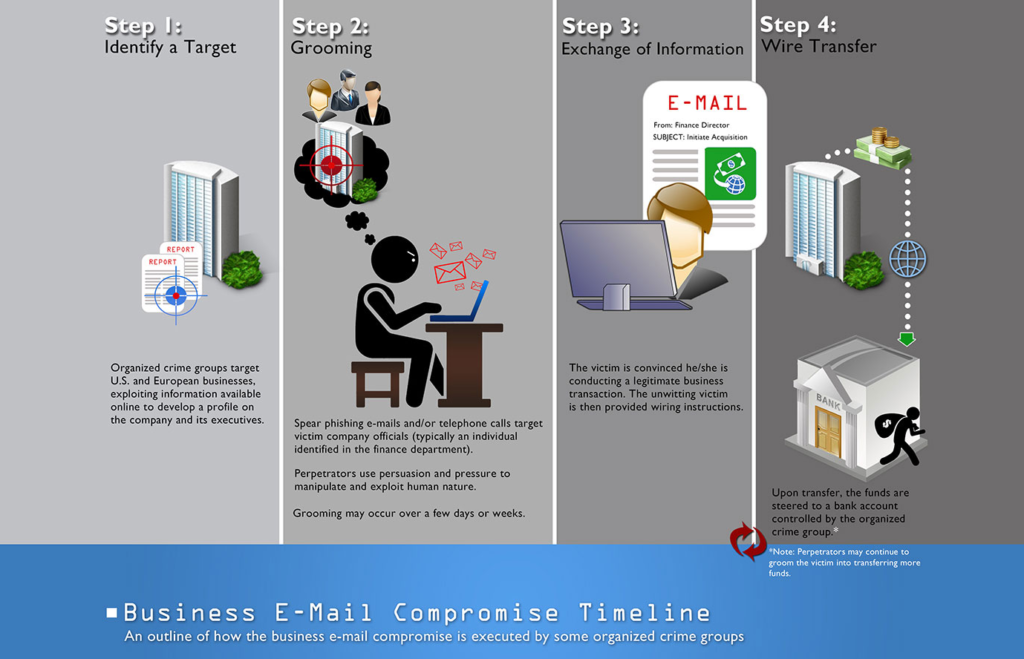
Normally, business email compromise scams involve cybercriminals pretending to be company CEOs, executives, vendors, etc., and emailing employees responsible for making payments and wire transfers with requests. Using various spoofing and phishing techniques, malicious actors are often successful in these attempts.
How business email compromise attacks are carried out
- Email/Website spoofing.
Because users are not always attentive when using email, it’s often not difficult to trick them into thinking fake emails are authentic. Slight changes to email addresses can go completely unnoticed to users if they don’t check carefully. For example, changing the letter “m” to “rn” can often be unnoticeable, depending on the font. A fullname@emailaddress.com address may be changed to fullnarne@emailaddress.com. Adding or removing letters also works to trick users.
Email spoofing is often used to target businesses. Malicious actors may spoof an email address of an executive and send directions to make a wire transfer to a company employee. The employee, who does not notice that the email address has been spoofed, may end up sending the money to the criminal’s accounts.
There is one famous case where a Lithuanian man was able to successfully defraud Google and Facebook out of $123 million by creating a company with a name similar to Quanta, a provider of hardware products. By sending fake invoices to both Google and Facebook and pretending to be from Quanta, he was able to trick employees into making transfers to bank accounts in Latvia, Cyprus, Hungary, Lithuania, Slovakia, and Hong Kong. The perpetrator was able to keep the scam running for three years until he was ultimately caught in 2017.
- Spear phishing.
Businesses are often a target of spear-phishing attacks that intend to steal sensitive/confidential data. While phishing attacks against regular uses are usually pretty generic and easily detectable, they are much more sophisticated when the target is someone specific, such as a business. The sender would make the email appear like it’s coming from a trustworthy source and trick the recipient into revealing confidential information, which can later be used in BEC attacks.
- Malware.
Malicious software can allow its operators access to a business’s highly sensitive data, such as email threads about invoices and billing. Once a cybercriminal gains access to the relevant email thread, they can then time fraudulent payment requests so that employees responsible for payments do not notice anything amiss. Malware can also allow its operators to steal users’ data and then try to extort companies for it.
How to protect yourself
- Always inspect the senders’ email addresses.
Whether the sender is familiar to you or not, always inspect their email address carefully. As we mentioned above, scammers slightly change legitimate-looking email addresses by adding, removing, or changing letters to make them seem authentic.
- Do not click on links and attachments in emails without double-checking.
Malicious emails usually come with links and/or email attachments, which is why it’s dangerous to interact with emails without double-checking first. If an email contains a link, hover over it with your mouse without clicking on it, and the address should appear at the bottom of your screen. If you click on the link and are taken to a site asking you to log in, inspect the site carefully and pay particular attention to the URL. Malicious actors are often able to copy legitimate websites exactly but the one thing that cannot be the same is the URL.
Because malware attachments can often carry malware, it’s strongly recommended that you always scan email attachments with anti-virus software or a service like VirusTotal before opening them.
- When possible, enable two-factor authentication (2FA) for accounts.
Unfortunately, 2FA is not always available but when it is, you must use it. It adds additional security to your accounts and prevents authorized access.
- Verify payment or purchase requests.
If you are asked to send a payment or make a purchase via email by your employer, double-check the payment in person. In case there is a change in a recurring payment, verify the changes in person.
- Do not give in to pressure to act quickly.
A common tactic used by malicious actors is to create a sense of urgency when making payment requests. Be especially wary if you receive an email asking for urgent payment, and always check that both the sender and the payment request are legitimate before doing anything.